A look at 2022 cybersecurity takeaways and how to start the New Year right.
A major lesson the private and public sectors can take away from 2022 is that as long as an organization or entity uses technology, it’s at risk for a cyberattack. And the reality is that as the sun sets on 2022, an organization can’t survive without technology. For that reason, cyber threats and cybersecurity are perhaps the most important topics to discuss with the dawn of the New Year—and perhaps every New Year.
Trends in AI (artificial intelligence) and ML (machine learning), quantum computing, supply chain management, blockchain, and the IoT (Internet of Things) are all linked by this underlying concern about security. A down economy, lack of a skilled cybersecurity workforce, lagging government policy, a large hybrid workforce, and the use of AI by adversaries will all affect the cyber scene in 2023.
Nasdaq’s October report that looks at 2022 cybersecurity in review says nearly every industry across the public and private sectors was affected by cyberattacks in 2022, including notable breaches in finance with the Coinbase breach announced in October, semiconductors with February attack on NVIDIA, automotive with the Toyota cyberattack in February, and education with the BlackCat (ALPHV) ransomware attack on North Carolina AT&T University in March. The tech sector was hit—for instance, there was the Microsoft breach—and cybercriminals also brought entire nations to their knees, as was the case in May when the Costa Rican government declared a state of emergency after a Conti ransomware attack.
Experts say to brace ourselves—this could all get worse before it gets better. And what will make it better? Policy needs to catch up. Basic cyber hygiene is still not ubiquitous, and that needs to change. Importantly, industries can’t wait for policy and expect it to solve everything. Every stakeholder needs to do its part, and cybersecurity needs to be a “people conversation,” not just a “technology conversation.”
2023 Trends through a Cybersecurity Lens
Bhavani Thuraisingham, computer science professor at the University of Texas at Dallas, founding executive director of the Cyber Security Research and Education Institute, and codirector of WiCyS (Women in Cyber Security) and WiDS (Women in Data Science), says tech trends to watch in 2023 include AI (artificial intelligence) and ML (machine learning), data science, cloud, IoT (especially in transportation and healthcare), quantum computing, and blockchain. But the underlying trend among all these trends, she says, is cybersecurity.
She lists three concerns in particular in the realms of quantum computing, supply chains, and AI/ML. First, Thuraisingham points to quantum. “Without a doubt, quantum computing is going to be a huge benefit to society due to its ability to process massive amounts of data and produce results in milliseconds that would have otherwise taken years to produce,” Thuraisingham says. “With respect to security, one of the major challenges we are faced with is ransomware attacks where hackers hold our data for ransom by encrypting our data and demanding payment in cryptocurrency before they return our data. Current encryption techniques would take millions of years to decrypt. However, with quantum computing, we can carry out decryption in milliseconds. This means ransomware attacks in their current form could be prevented. However, what does this mean for security? We will not be able encrypt any data. This would mean we will not have any security. Therefore, there is a lot of work now on post-quantum cryptography. That is, developing encryption techniques that would work after quantum computing becomes a technology that we use daily. The goal is to develop encryption techniques that cannot be decrypted in milliseconds due to quantum computing.”

The next cybersecurity trend Thuraisingham mentions is the idea that cyber resilience in supply chains is going to gain importance in 2023 and beyond. “Our supply chains have been significantly impacted due to the pandemic,” she says. “Furthermore, the supply chain software systems are susceptible to cyberattacks as the parts come from different countries where we cannot trust the software. Therefore, security concerns have increased significantly for supply chain management. The challenge for us is how do we build resilient supply chain management systems? That is, even if the software components of the supply chain are compromised, how can the system as a whole be resilient? Understanding the security risks and developing supply chain systems that are resilient to cyberattacks will be a major consideration.”
Her third point and warning for 2023 is that AI/ML techniques can be attacked. “(T)he adversary may observe the data we are utilizing to train the models and learn about our models (and then) thwart the data and/or the models,” Thuraisingham explains. “This means the results we obtain are going to be highly erroneous, resulting in catastrophic consequences. Therefore, the AI/ML techniques have to be secure.” She further predicts there will be development in the realm of trustworthy and scalable AI/ML techniques in which the AI/ML techniques have to scale, recover from cyberattacks, and produce results that are accurate, do not discriminate, and yet maintain the privacy of individuals.
Richard Forno, principal lecturer in the UMBC (University of Maryland, Baltimore County) Dept. of Computer Science and Electrical Engineering and assistant director of the UMBC Center for Cybersecurity, also points to AI and ML trends manifesting in the cyber space. “We are seeing increased use of AI and ML to launch all types of more intelligent and more targeted cyberattacks, ranging from traditional network attacks to more sinister data-mining to craft very convincing phishing attacks,” Forno says. “I’m also concerned at how AI/ML is being used to create ‘deep fakes’ of audio, video, and images—are we teaching people and society how to identify them through critical thinking and media literacy in schools? Sadly, mostly not. This will only get worse in the coming years.”
As a reaction to the growing threats of increasingly sophisticated cybercriminal tactics, Kevin Curran, professor of cybersecurity at Northern Ireland’s Ulster University, anticipates activity around HE (homomorphic encryption) and zero-trust architectures in 2023. “The most impactful 2023 development is likely to revolve around privacy-preserving technologies. In particular, HE, which allows processing data whilst encrypted at rest thus allowing new scenarios where third-party cloud providers have no insight into the data at any point,” he says. “Although the technique has been known for about 20 years, it has only been in recent times that HE libraries have achieved near-realtime speeds, which enable real-world applications to utilize.”
Curran points to companies like Vaultree that fully encrypt data client-side, allowing for realtime scalable data processing and computations. “Given the fact that data is processed in unencrypted form, it is quite common for attackers to target data in use, rather than targeting data, which is encrypted during storage and transit,” he explains. “That is where modern techniques such as HE could be considered as data can be processed while encrypted. In general, the rise of low-ease-of-use privacy preserving APIs to encrypt data at rest will become more widely adopted.” Zero-trust cloud security architectures will also become more mainstream. “The pandemic speeded up many organizations and 2022 saw (zero trust) become more popular,” Curran says. “It is a security architecture for a modern remote workforce. The need for a zero-trust security model has arisen in part because enterprises no longer tend to host data in-house bur rather through a variety of platforms and services which reside both on and off premise with a host of employees and partners accessing applications via a range of devices in diverse geographical location. This is what companies desire in the pandemic. The traditional security model is no longer fit for purpose and zero-trust models are simply more relevant in this era.”
Takeaways and Creating Positive Momentum
In preparation for 2023, it’s worth considering what, if anything, industries learned in 2022. Josephine Wolff, associate professor of cybersecurity policy, computer science, and engineering at Tufts University, says the past year has shown how effective tending to the basics can be. “One of the lessons of 2022 is simply that organizations can be quite effective at thwarting many cyberattacks if they adhere to basic cyber hygiene principles and best practices,” Wolff explains. “Surprisingly, warnings earlier this year about Russian cyberattacks have led to relatively few successful intrusions, suggesting that increased vigilance and security measures may make a significant difference.”
Ryan Calo, professor in the School of Law, adjunct professor in the School of Computer Science and Engineering, and adjunct professor in the Information School at the University of Washington and faculty cofounder at the Tech Policy Lab, says lawmakers and agencies such as the Federal Trade Commission are becoming more assertive when it comes to issues of privacy and antitrust. “This pressure could lead to more responsible innovation as we transition to new types of digital interactions and products,” Calo says. “2022 was a year that finally drove home concerns about misinformation and other information-based harms. It felt like a turning point from the laissez-faire days of internet governance since the 1990s.”
The government will certainly play a role in what the cybersecurity landscape looks like in 2023. Wolff says she expects to see more mandatory reporting of different types of cybersecurity incidents. Similarly, Lauren Van Wazer, vice president of global public policy for Akamai, says the regulations around cyber-incident reporting are siloed and more work needs to be done to reconcile disparate reporting requirements. Van Wazer also points to the Biden Admin.’s May 2021 executive order pushing federal agencies to adopt zero-trust network architectures—a positive step contributing to the trend pointed out by Ulster University’s Curran.
5 Tips for Taking Cybersecurity Seriously in 2023
- Don’t discount or ignore basic cyber hygiene. It makes a big difference.
- Get cybersecurity in the boardroom and ensure cybersecurity is playing a key role in corporate governance.
- Assume this is true: Cyberattacks will never stop. Cybersecurity is always a top priority (every quarter, every year, always).
- Invest in cybersecurity, including solutions and staff. Analyze risk regularly and create a plan for managing cyber risks
- Treat cybersecurity as a “people conversation” and not just a “technology conversation.” Train up existing staff and hire security experts whenever possible.
What’s more, the economy’s impact on cybersecurity shouldn’t be ignored in the outlook for 2023. “The amount of cyber infrastructure—including technology, training, and personnel—organizations are willing to invest in over the next 12 months is likely to shrink,” Van Wazer says. “This will open up opportunities for cybercriminals and potentially lead to more hacks and data breaches.”
As technology accelerates, it also creates new avenues for cyberattacks. By incorporating good cybersecurity oversight and governance, though, organizations can address these risks. Meanwhile, the government is enforcing various policies for cybersecurity, but as a general rule, policy lags behind technology innovation. UMBC’s Forno says: “We need lawmakers who are objectively informed about technology and act from that perspective versus trying to frame technology policy through a partisan lens or special-interest talking points.”
James Hendler, professor and AI researcher at Rensselaer Polytechnic Institute and chair of the Technology Policy Council for the ACM (Assn. for Computing Machinery), says cybersecurity issues will probably get worse before they get better. “We really need government involvement, and right now there’s not a clear mandate in the legislative—as opposed to executive—branch to really change things,” Hendler explains. “The good news is that as people move to more and more cloud-based services, the cybersecurity teams at the big companies are able to do way more than the individual companies. However, the individual responsibility to make sure connections are secure, to learn to avoid phishing attacks, etc., also grows. So, we need to learn to share responsibilities—attacks like the Colonial Pipeline ransomware show us that the interconnectivity comes with responsibility on all sides.”
Akamai’s Van Wazer says in recent history, it’s become clear that organizations in all industries need a plan for how they will manage cyber risks. “We have seen every industry and size of organization targeted by cybercriminals and ransomware attacks, and that is unlikely to change anytime soon,” she says. “In 2023, organizations must address cyber competency and manage cyber risks to avoid becoming the next Colonial Pipeline. And this is a people conversation, not just a technology conversation. Investing in cybersecurity hires and organization-wide training is just as important as implementing the right technology tools.”
Key to success will be providing enough support for cybersecurity. Organizations need to train up their staff and hire security experts, which can admittedly be hard to find. And basic hygiene is anything but “basic”. Rather, it’s crucial and undervalued as a strategy against cyberattacks. UMBC’s Forno says a major, ongoing problem is that most cyber incidents tend to be easily preventable and are often self-inflicted. Why? Because too many organizations are failing to implement basic IT management or cybersecurity recommendations.
Finally, in 2023, get those CISOs (chief information security officers) more involved in executive committees. By getting “cybersecurity in the boardroom”, the University of Texas at Dallas’s Thuraisingham says organizations across the private and public sectors can better set themselves up for success in the New Year. As long as an organization uses technology, cyberattacks will never stop. And in today’s hyperconnected world, an organization cannot survive without technology. Therefore, it’s imperative organizations see cybersecurity as a top priority for 2023 and every year.
Links for Further Learning:
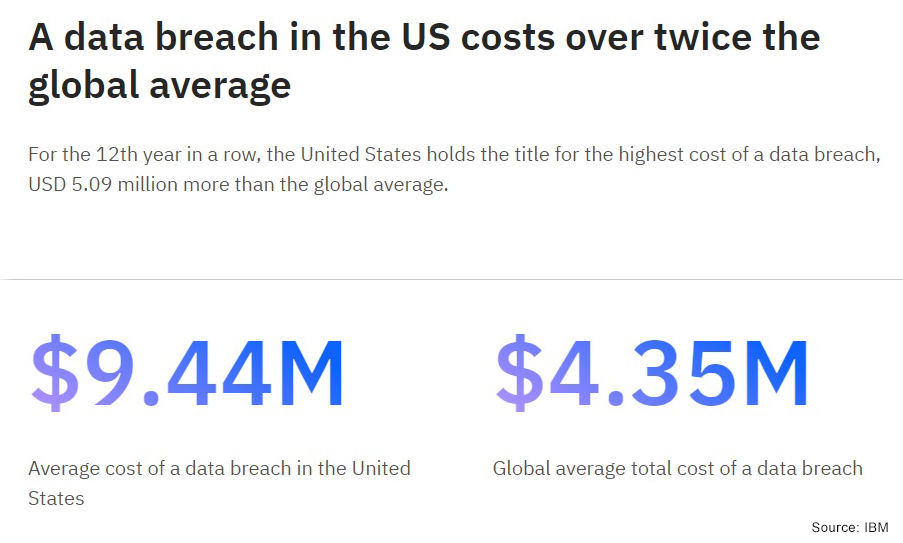
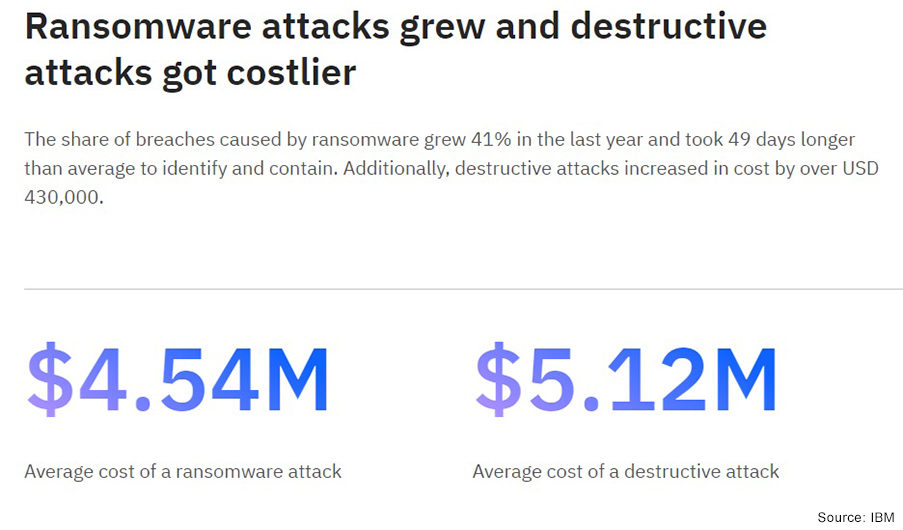
- IBM’s Cost of a data breach 2022
- Nasdaq’s 2022 Cybersecurity: A Year in Review
- Executive Order on Improving the Nation’s Cybersecurity
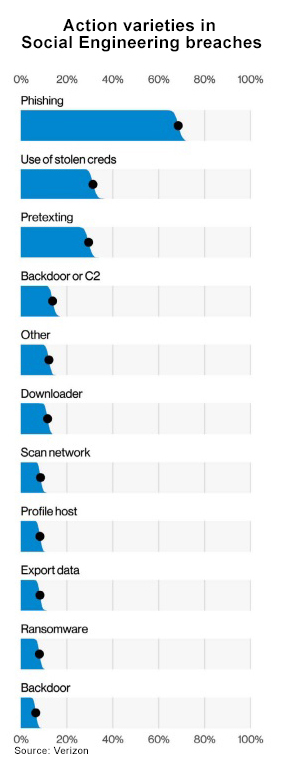
- Verizon’s 2022 Data Breach Investigations Report
- Is Tricking a Robot Hacking?
Want to tweet about this article? Use hashtags #IoT #sustainability #AI #5G #cloud #edge #digitaltransformation #machinelearning #infrastructure #bigdata #blockchain #cybersecurity #security #cyberattacks #databreach #ransomware #artificialintelligence #ML #quantum #policy #Vaultree #Akamai


